jtsec, Blog
Par un écrivain mystérieux
Last updated 16 juin 2024

While performing a STIC evaluation of a product, the evaluation team at jtsec thought that it would be interesting to analyze the communications between two embedded devices that were part of the product. The main objective was to determine whether those communications were properly secured with encryption and other important security measures when it comes to devices that communicate using radio frequencies such as protection against jamming, GPS spoofing or replay attacks.

jtsec Beyond IT Security on X: The development of a patch

jtsec, Blog

jtsec, Blog

2021 Common Criteria Statistics Report - CCLab News

jtsec Beyond IT Security on LinkedIn: jtsec, Blog

Salario en JTSEC Beyond IT Security - informe sobre salarios - GoWork

jtsec, Blog

ICCC2023 Statistics Report, has Common Criteria reached its peak

Antonio Cortes on LinkedIn: jtsec, Blog

jtsec Beyond IT Security on LinkedIn: jtsec, Blog

jtsec, Blog

jtsec Beyond IT Security on LinkedIn: jtsec, Careers

jtsec Beyond IT Security

jtsec, Blog
Recommandé pour vous
 HackRF One Bundle14 Jul 2023
HackRF One Bundle14 Jul 2023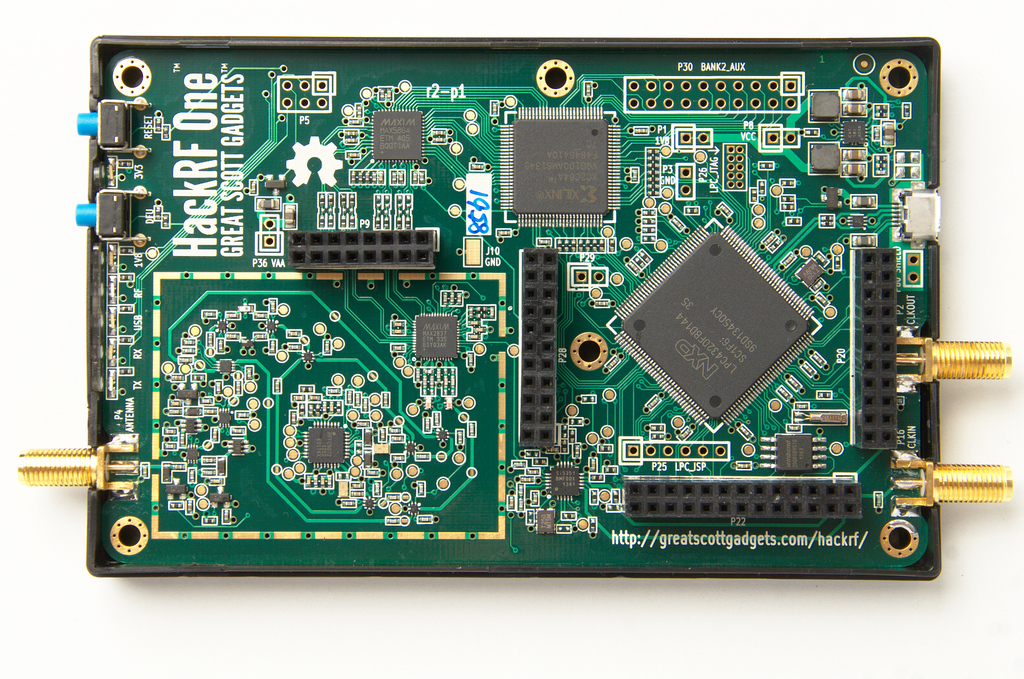 HackRF One — HackRF documentation14 Jul 2023
HackRF One — HackRF documentation14 Jul 2023- What I can do with HackRF One? All I can see on the internet is14 Jul 2023
 Hackrf One Rtl Sdr Software Defined Radio Us - Voice Recognition14 Jul 2023
Hackrf One Rtl Sdr Software Defined Radio Us - Voice Recognition14 Jul 2023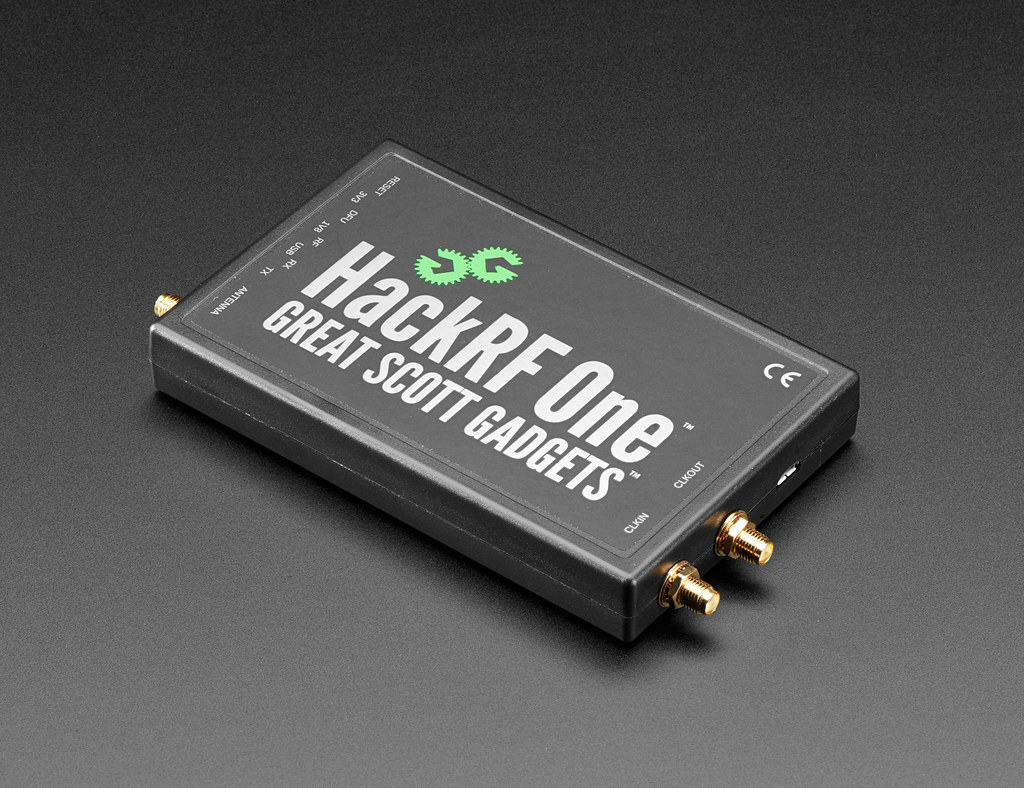 HackRF Guide: Mastering Modern Radio Hacking Fundamentals14 Jul 2023
HackRF Guide: Mastering Modern Radio Hacking Fundamentals14 Jul 2023 Hackspyhackrf One Sdr Development Board - 1mhz-6ghz Usb2.0 Rtl14 Jul 2023
Hackspyhackrf One Sdr Development Board - 1mhz-6ghz Usb2.0 Rtl14 Jul 2023 PISWORDS - Hackrf One14 Jul 2023
PISWORDS - Hackrf One14 Jul 2023 Nooelec - HackRF One - RF Shield & Component Kit14 Jul 2023
Nooelec - HackRF One - RF Shield & Component Kit14 Jul 2023- HACKRF as half duplex transceiver for qo100 and hF, how to14 Jul 2023
 HackRF One - ACG 15014 Jul 2023
HackRF One - ACG 15014 Jul 2023
Tu pourrais aussi aimer
 Jeu de société stratégo junior14 Jul 2023
Jeu de société stratégo junior14 Jul 2023 RADIATOR BOOSTER VENTILATEUR DIFFUSEUR DE CHALEUR POUR RADIATEUR À EAU Comparer les prix de RADIATOR BOOSTER VENTILATEUR DIFFUSEUR DE CHALEUR POUR RADIATEUR À EAU sur Hellopro.fr14 Jul 2023
RADIATOR BOOSTER VENTILATEUR DIFFUSEUR DE CHALEUR POUR RADIATEUR À EAU Comparer les prix de RADIATOR BOOSTER VENTILATEUR DIFFUSEUR DE CHALEUR POUR RADIATEUR À EAU sur Hellopro.fr14 Jul 2023 THRUSTMASTER - Pédale et volant T300RS pour PC, PS3 et PS4 - Noir14 Jul 2023
THRUSTMASTER - Pédale et volant T300RS pour PC, PS3 et PS4 - Noir14 Jul 2023- Extinction Code Pack - Epic Games Store14 Jul 2023
 Housse Protection pour Coussin Jardin Sac Rangement pour Meubles14 Jul 2023
Housse Protection pour Coussin Jardin Sac Rangement pour Meubles14 Jul 2023 Get your little ones excited for Christmas with these 7 great14 Jul 2023
Get your little ones excited for Christmas with these 7 great14 Jul 2023 Batterie pour Aspirateur Balai Sans Fil Dyson DC58,DC59,DC61,DC62,DC72,DC74 (2500mAh)14 Jul 2023
Batterie pour Aspirateur Balai Sans Fil Dyson DC58,DC59,DC61,DC62,DC72,DC74 (2500mAh)14 Jul 2023 COSTWAY Mini Réfrigérateur Portable Fonction Chaud et Froid -314 Jul 2023
COSTWAY Mini Réfrigérateur Portable Fonction Chaud et Froid -314 Jul 2023 Poulet à la sauce aigre-douce (Chine) : Recette de Poulet à la sauce aigre- douce (Chine)14 Jul 2023
Poulet à la sauce aigre-douce (Chine) : Recette de Poulet à la sauce aigre- douce (Chine)14 Jul 2023 Blezliving® 2 pièces Set de housse de protection pour robinet14 Jul 2023
Blezliving® 2 pièces Set de housse de protection pour robinet14 Jul 2023
